El término ‘egosurfing’ proviene del latín ‘ego’ que significa ‘yo’, y del inglés ‘surfing’, que se traduce como ‘navegar/surfear por Internet’. Todos, o casi todos, alguna vez hemos buscado nuestros datos en la red, y es una buena práctica para conocer la seguridad de los mismos en Internet. En este artículo vamos a ver cómo realizar egosurfing en nuestra empresa de manera segura.
Hay tres formas de practicar egosurfing en nuestra empresa:
Búsqueda en Internet
Da igual el navegador o buscador que utilicemos. Escribir directamente el nombre de nuestra empresa entre comillas hace que la búsqueda sea más directa y concreta y sólo busque los parámetros entrecomillados. No solo tenemos que quedarnos con las primeras páginas de resultados. Tenemos que indagar e inspeccionar las páginas de vídeos, imágenes, noticias… así estaremos maximizando el flujo de información disponible en la red. También es muy pero que muy importante no quedarnos solo con el nombre de la empresa. Hay que buscar otros datos que nos identifiquen, tales como la dirección postal, correo electrónico corporativo, CIF…
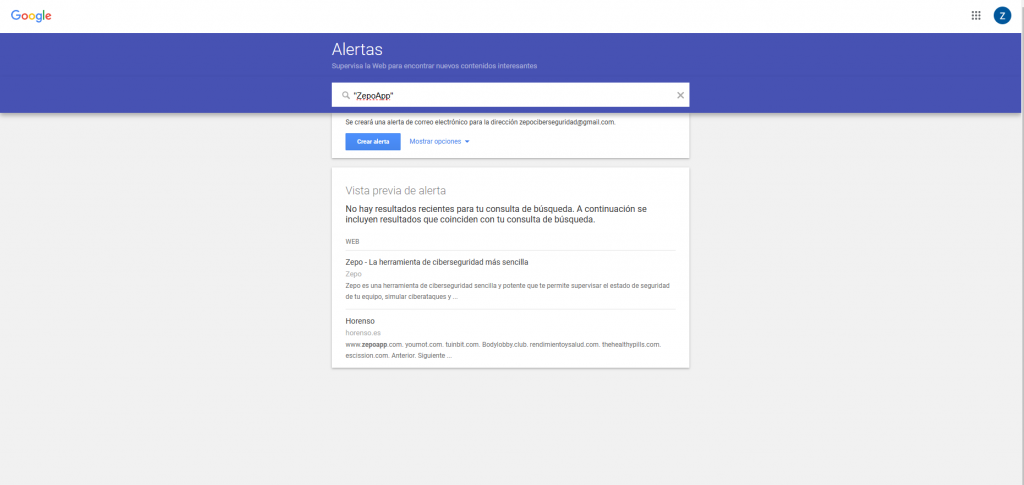
Google Alerts
Esta magnífica herramienta nos permite configurar previamente las notificaciones si alguien busca en Internet los parámetros que hemos seleccionado. De esta forma, podemos seleccionar los datos de nuestra empresa que comentábamos antes y seleccionar a qué correo y con qué frecuencia nos llegarán las alertas. Esta es una fantástica forma de comprobar nuestra privacidad y seguridad en la red.
Redes Sociales
Esta estrategia es similar a la de búsqueda en navegadores. Es muy importante buscar el nombre de nuestra empresa en todas las redes sociales que tengamos, pues la posibilidad de que aparezcan perfiles falsos que publiquen contenido en nuestro nombre es muy elevada.
Una cosa que no hay que pasar por alto a la hora de buscarnos en redes sociales es el nombre de la cuenta y de nuestra empresa. Si por ejemplo nuestra empresa se llama ‘ZepoApp’, debemos probar diferentes combinaciones de nombres en el buscador de la red social, tales como: ‘zepoaplicación’, ‘appzepo’, ‘zepoapk’, etc… Parece una tontería, pero estas diferencias pueden hacer que los ciberdelincuentes nos suplanten la identidad, pudiendo pedirles a nuestros clientes datos sensibles en nuestro nombre o haciéndoles phishing (haciéndoles creer que por ejemplo han ganado un sorteo), desprestigiando el nombre de nuestra empresa.
Y, ¿si lo que he encontrado en mi empresa no quiero que esté publicado?
En primer lugar, si la información que hemos encontrado fue publicada por nosotros mismos, únicamente debemos eliminarla de la red social o plataforma en la que se encuentre.
En segundo lugar, si esa información no la hemos publicado nosotros, tenemos varias opciones:
- Por ejemplo, si es un comentario malintencionado o nos han etiquetado en una publicación sin nuestro permiso, podemos configurar nuestros perfiles para bloquear ciertos comentarios y permitir quiénes nos etiquetan o no.
- Si la información que hemos encontrado vulnera el honor, reputación y/o privacidad de nuestra compañía, debemos solicitar directamente al responsable o administrador del perfil o página web, que elimine el contenido. Si entendemos que la difusión de dichos datos va en contra del honor de nuestra empresa y pudiera ser constitutivo de delito, podríamos interponer una denuncia.
En resumen, si vemos un perfil falso que se hace pasar por nuestra empresa o alguno de nuestros empleados, debemos denunciarlo directamente a la red social pertinente a través de todos los canales puestos a disposición para ello.
Con Zepo. puedes desarrollar una cultura de ciberseguridad sostenible dentro de tu organización en 3 simples pasos:

Da de alta a tus empleados.
Puedes hacerlo de forma manual o a través de un CSV

Lanza ataques y pon a prueba a tus equipos.
Podrás comprobar en tiempo real quiénes caen en la trampa

Fórmales en prevención de ciberataques.
Crea cursos personalizados en materia de prevención