The world today is completely interconnected, so no company is safe from cyberattacks. This means that choosing the right cybersecurity software can make all the difference between being well protected and being completely – and possibly unknowingly – vulnerable.
Stay tuned to find out which cybersecurity software can best defend your organization.
In the digital age in which we live, data and information have become crucial assets for both individuals and companies. However, this information and technology boom has also given rise to a growing threat: cyberattacks.
Cybersecurity software has emerged as a protective shield against that threat, playing an essential role in protecting our digital assets and our online privacy.
What are cybersecurity software solutions?
Cybersecurity software is a set of tools, techniques, and processes designed to protect computer systems, networks, devices and data against cyber threats.
These threats can range from viruses and malware to hacker attacks, identity theft, ransomware, and cyber espionage. Cybersecurity software acts as a virtual shield that defends our digital world from potential attacks and vulnerabilities.
Why is it crucial to have cybersecurity software in your company?
- To protect your information: From personal and financial information to sensitive business data, all companies have information that they need to protect. This is essential to prevent theft, manipulation, or destruction by cybercriminals.
- To prevent cyberattacks: Cybersecurity software acts as a crucial barrier to prevent these attacks and minimize their impact.
- To avoid disruptions to business operations: Disruptions in the technology infrastructure can have serious consequences for companies.
- To protect your company’s reputation: Cybersecurity incidents can severely damage your organization’s reputation. Relationships: Having robust cybersecurity software in place demonstrates a commitment to the security of your customers and business partners.
- To comply with current regulations: Many industries and organizations are subject to strict regulations regarding data security. Implementing adequate cybersecurity software is essential to comply with these regulations and avoid legal sanctions.
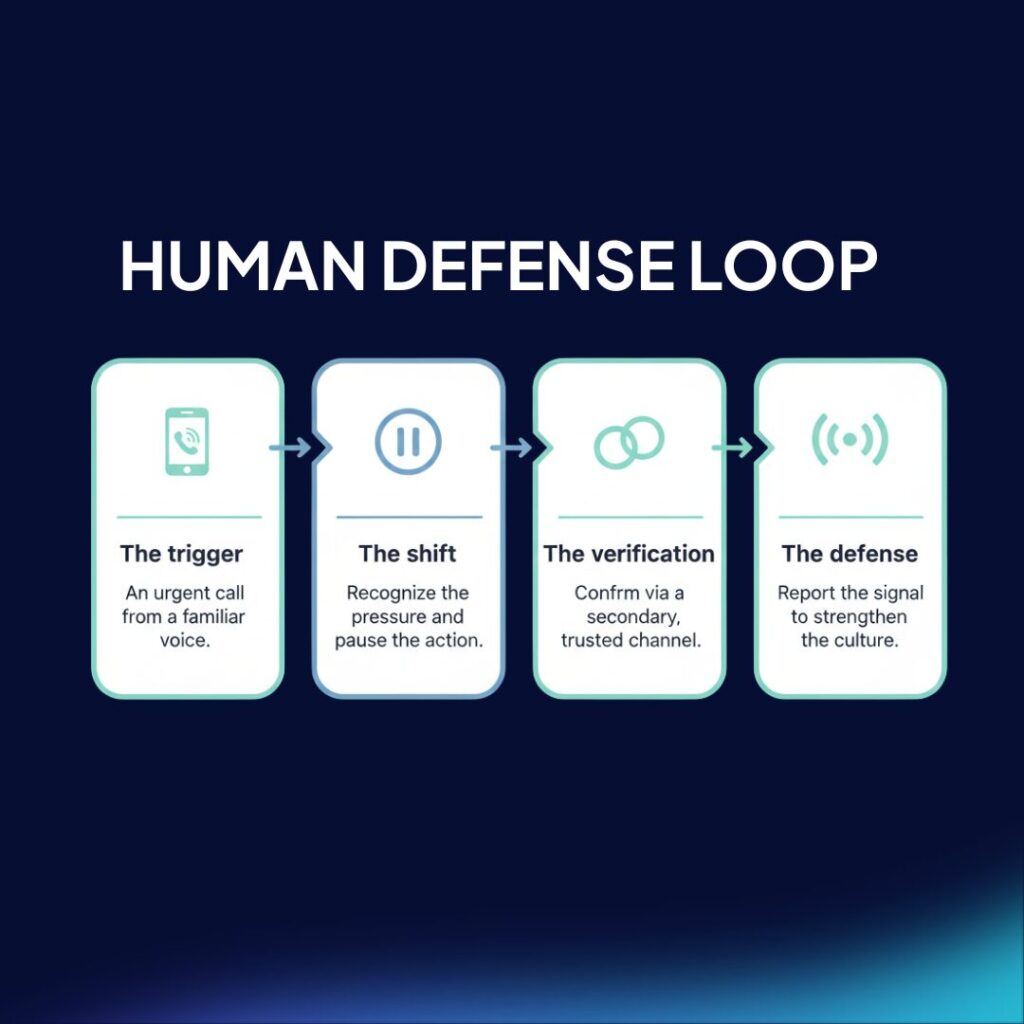
Those five reasons for having at least one cybersecurity software service are compelling, but here’s the most important one: because of the human factor. People are always the weakest link in a corporate cybersecurity strategy.
Despite the efforts of organizations to improve the digital security of their assets, potential threats continue to increase, most of which start with social engineering techniques, with people at the center of their strategy. For this reason, you need a strong first – and last – line of defense, a human firewall.
A human firewall represents the ultimate security barrier for any company or organization. These individuals are responsible for counteracting potential threats that could endanger the company’s assets.
An effective human firewall is achieved through education and the promotion of cybersecurity awareness in the business environment. This is because the human component is the most vulnerable point, as it is susceptible to the social engineering tactics that cybercriminals use to trick us. Overcoming that vulnerability necessitates education and a culture of cybersecurity.
To clarify, the objective of the human firewall is the creation of an individualized chain adapted to each employee, since each person has a different set of skills and sits at a different level in the company.
What types of cybersecurity software are there?
Antivirus
This is designed to detect and remove viruses, malware, Trojans, and other types of malicious software that can damage your system or steal sensitive information.
Intrusion Detection Programs (IDS)
These constantly monitor activity on your network for unusual patterns or behavior that may indicate an attack. IDSs can be host-based (HIDS) to monitor individual devices or network-based (NIDS) to monitor network traffic.
Firewalls
Firewalls are an essential barrier between your network and the outside world. They can be hardware or software and act by filtering network traffic to allow or block certain connections according to predefined rules.
Firewalls are therefore essential to protect your network against unwanted intrusions.
Anti-Malware Software
These programs focus on specific threats that may not be detected by traditional antivirus software.
Data Loss Prevention Programs (DLP)
DLP programs focus on preventing sensitive data from leaving your organization without authorization. In short, they control and supervise the transfer of data, preventing leaks of confidential information.
Two-Factor Authentication (2FA) programs:
Two-factor authentication is an additional layer of security that requires users to provide two different forms of authentication before accessing an account or system. That means even if criminals get hold of passwords, they can't automatically gain access to accounts.
Password Management Software
These programs store and generate secure passwords for online accounts.
They therefore help ensure that strong, unique passwords are used for each service, reducing the risk of unauthorized access.
Vulnerability Analysis Software
These tools identify and assess weaknesses in your systems and networks, allowing you to correct them before they are exploited by cybercriminals.
Cloud Security Software
Cloud security programs protect your data and applications hosted on cloud platforms, ensuring they are safe from cyber threats.
Incident Response Programs (IR)
IR programs help organizations prepare for, manage, and recover from security incidents. This includes detection, containment, and mitigation of cyber threats.
What are the characteristics of a good cybersecurity program?
Not all cybersecurity software is created equal. The best applications share a number of key features that make them effective in protecting your systems, networks, and data against ever-evolving cyber threats. Here are the most important features to look for in cybersecurity software:
- Real-time detection: Cybersecurity software must continuously monitor activity in real time to identify suspicious behavior and stop attacks in their early stages.
- Regular updates: Regular updates of virus signatures and threat databases ensure that the program can recognize and defend against new threats.
- Multi-layered protection: Effective cybersecurity software uses a variety of techniques and layers of security to protect against different types of threats. This can include antivirus, firewalls, intrusion detection and more.
- Machine Learning: Artificial intelligence and machine learning enable cybersecurity software to adapt and improve its detection capabilities as it learns from previous behavioral patterns and threats.
- Customizable firewalls: Firewalls should allow customized configurations to suit the specific needs of your network and applications, authorizing only legitimate traffic.
Current trends in cybersecurity software
Despite the features and integrations offered by a wide range of cybersecurity programs, new software is being released that can adapt to current trends in cyber defense.
This ability to adapt is essential. One example of software that does this are the cybersecurity programs dedicated to perform phishing simulations with an organization’s employees, as we do in Zepo.
These programs are focused on the training and awareness of a company’s employees and are able to measure the company’s risk level and how aware and trained the employees are.
Regarding the measurement of cyber risk in companies, Cristina Dolan, Global Head of Alliances at RSA NetWitness, has already warned that the proliferation of new technologies is leading to the development of new types of attacks.This makes us more vulnerable to cybercriminals.
These new technologies include Artificial Intelligence, cloud data security, and mobile security.
With Zepo, you will be able to build a real human firewall.

Register your employees.
You can do this manually or through a CSV.
You can create groups of employees based on their level of knowledge and awareness of cyberattacks.

Launch attacks and test your teams.
You will be able to check in real time who falls into the trap.
We create customized templates for your campaigns based on the banks and suppliers you work with. No one will know that it is a simulation.

Train your staff in cyberattack prevention.
Create customized courses on prevention. 3 minutes per month.
No more boring mandatory courses. With Zepo, you will learn and have fun at the same time.