Cyber-attacks continue to increase in both volume and vector. We may not want to face it, but that is the reality. Cybercriminals are increasingly taking advantage of complex and volatile human emotions to gain access to their victims’ sensitive data.
In this article, we analyze a few the emotions that cybercriminals seek to arouse in their victims through social engineering techniques.
We live in a constantly evolving digital world, and yet social engineering– based simply on understanding how people work – has become one of the most sophisticated and deceptive threats we face in cybersecurity.
Cybercriminals have perfected their techniques, exploiting not only technical vulnerabilities, but also our own psychology. In this exciting journey through the dark side of the internet, we will explore how attackers use human emotions as their secret weapon in social engineering.
From fear to curiosity, greed to compassion, we will unravel the strategies cybercriminals use to manipulate their victims and get their hands on valuable personal data.
1. Fear, the most powerful social engineering technique.
Kevin Mitnick, a world-renowned hacker, early on acquired the ability to employ emotions as a manipulation tool in his social engineering strategy.
During that period, his main focus was system administrators, and his approach to social engineering began with telephone contact.
Kevin used fear as his favorite emotional resource, as he recounts in his book, “Ghost in the Wires”.
“I would call the company I had targeted, ask for their computer room, make sure I was talking to a systems administrator, and say, ‘This is [any fictitious name that came to my mind at that moment], from DEC technical support. We have discovered a catastrophic bug in your version of RSTS/E. You could lose your data.’ You could lose your data“, Kevin said in his book.
When the person is sufficiently frightened, he would say: “We can patch your system without interfering with your operations.” “At that point, the guy (or, sometimes, the woman) could hardly wait to give me the phone number and access to the system administrator’s account.”
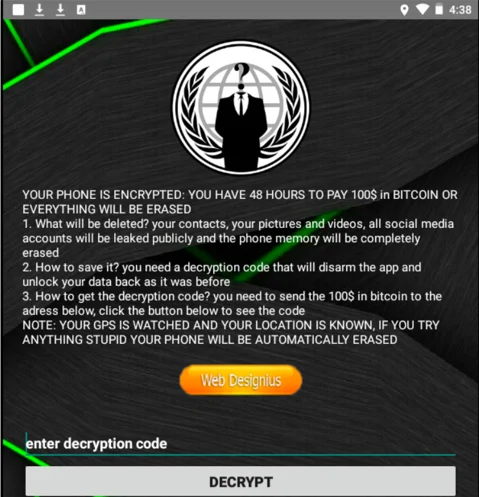
What do we see in this example? A feeling of fear. ‘You have 48 hours to pay $100 in bitcoin or you will lose all your data.’ It’s simple psychology: cybercriminals scare you into acting fast.
In other words, cybercriminals often play on emotions that complement each other: urgency and fear.
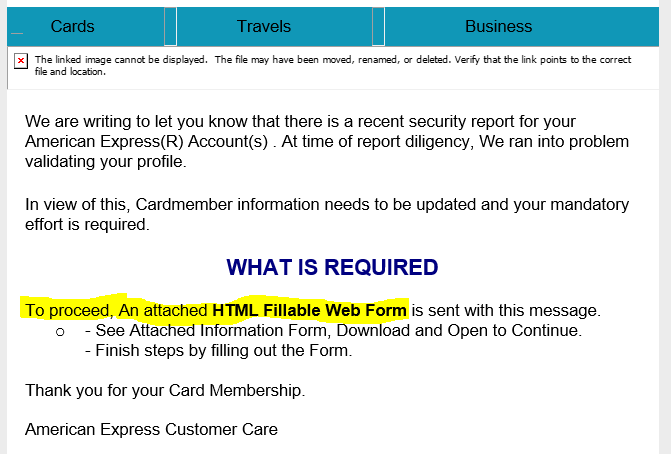
Here’s an example of a scary situation involving the security of credit accounts.
Have you received a security report regarding your American Express account? Your account may be closed if you do not take action.
To continue, you just need to open and complete the attached web form. Unfortunately, the fear and desire to fix things fast makes it easier for cybercriminals.
It is important to note the persistent phishing tactic used in the message: “someone has accessed your account”. You are prompted to enter your username and password to find out who has logged in.
2. Sense of urgency: act NOW
“Answer now”, “quickly”, “don’t delay any longer”, among other expressions, indicate a feeling of acting fast, that time is running against you.
It is common to find false security alerts that include exclamation points. This situation generates a sense of urgency, such as the following: “Your iCloud, photos and contacts are at risk! Act now to prevent a virus from deleting and stealing them”.
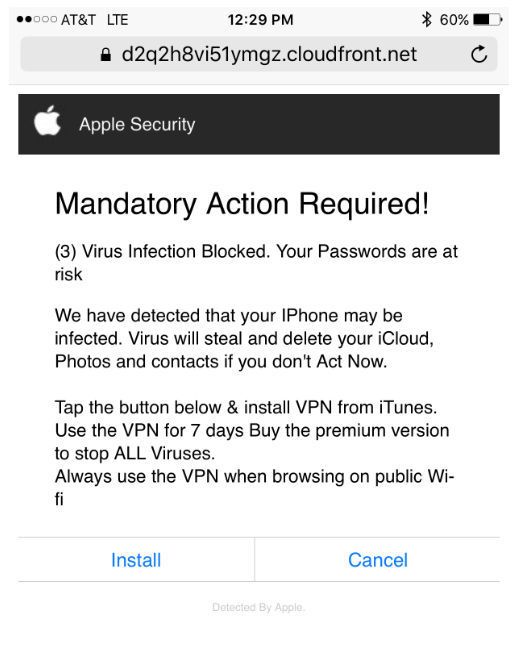
Notably, these alerts often incorporate two attractive buttons inviting you to click, which increases the risk of falling for a phishing attack.
You may be called to make a decision between “Install” and “Cancel”, but be aware that both options can be traps set by hackers.
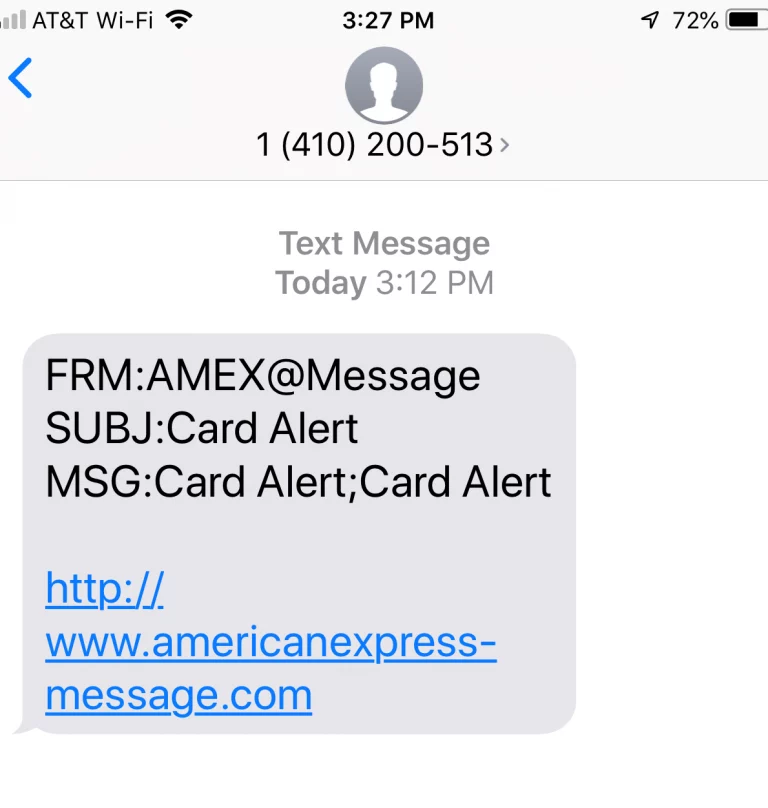
Looking at this other example of phishing via SMS (also called smishing ), where the sense of urgency is evident.
First, if the Card Alert is mentioned three times, it is clear that American Express has a legitimate reason to contact you.
Similarly: Most employees may not notice that the letter “s” is missing at the end of “http://”, which denotes a lack of security, since all companies, and especially banks, must use the secure https protocol indicated in the URL, which guarantees the security of the web page.
It is important to recognize that credit card companies are sending out a large number of alerts today.
3. Curiosity killed the cat… and let the cybercriminal win.
Curiosity is an intrinsic part of being human.
However, cybercriminals love using social engineering techniques to manipulate those human facets, to arouse the curiosity of their potential victims to fall for a scam so they can get hold of your personal data.
Let’s look at a couple of examples to get a better understanding:
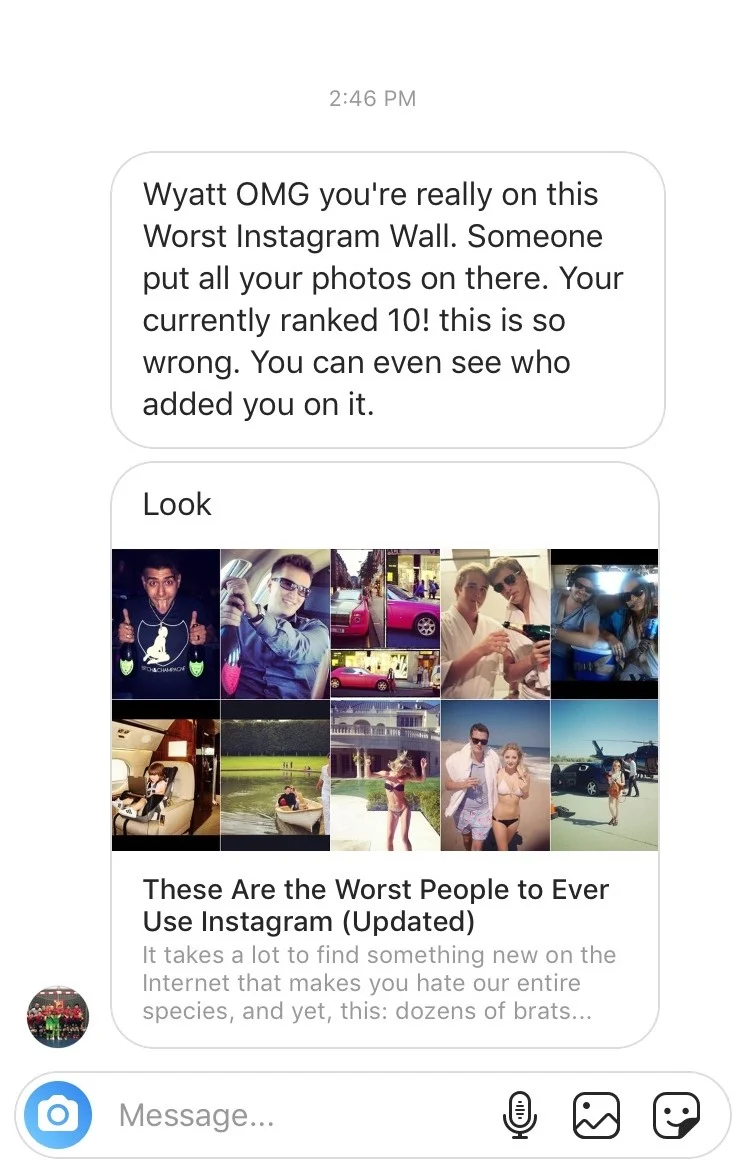
When you receive a message that says, “OMG, you’re on the worst Instagram page; someone has posted all your photos there,” it’s natural to feel some trepidation. However, perhaps it’s the final sentence that most tempts you to click: “You can even find out who posted you!”
Now, the question arises as to whether this can be true. Curiosity can be a powerful force that influences your end users’ decision making.
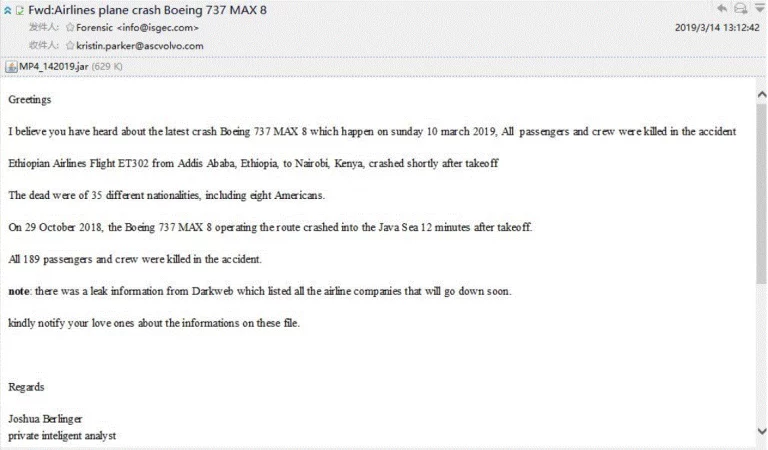
Curiosity and social engineering in air crashes
Continuing with another example of “curiosity”, the quality may have been low, but its relevance was extraordinarily high. It happened after the second accident involving the Boeing MAX 8and involved e-mails that contained an attachment allegedly leaking information about the risks of flying on these planes.
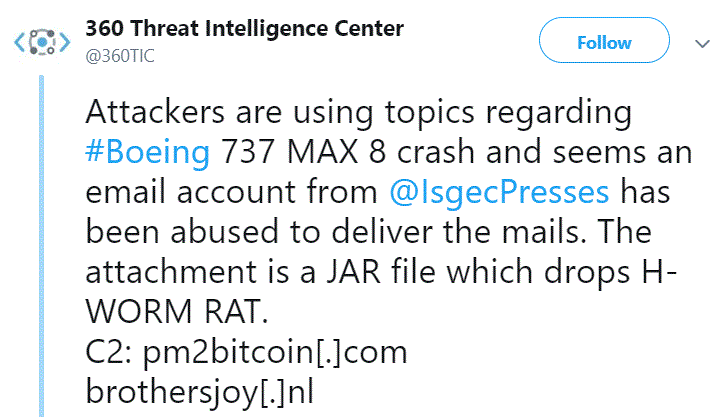
However, 360 Threat Intelligence Center, the research division of 360 Enterprise Security Group, posted on its official Twitter account, warning users not to fall for this scam.
4. Greed
Similarly, cybercriminals seek to awaken in their victims a sense that they can win or gain something, coupled with a sense of urgency.
If you act NOW, you can win this or that – but you have to click on the link (which is malicious) as soon as possible, otherwise you will not be able to benefit from the supposed prize.
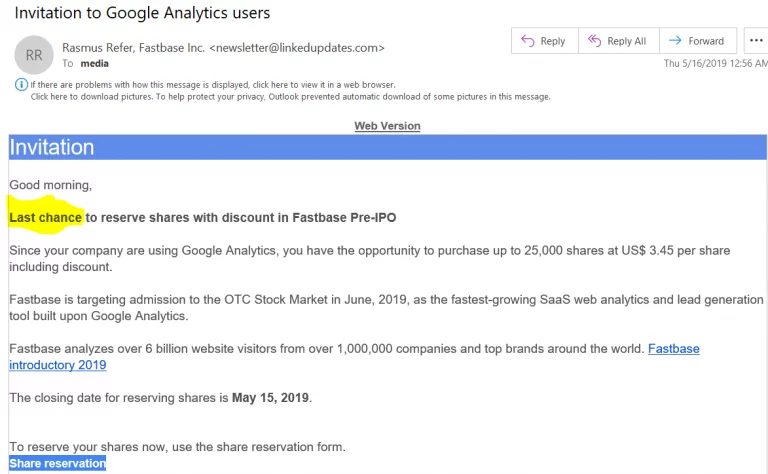
We see in this email several things that lead us to believe that it is a scam:
- ‘Last chance’: You’re immediately being rushed into something you didn’t ask for or have anything to do with. When we see a sense of urgency and greed, we should immediately assume that it is most likely a social engineering scam.
- Making money: Cybercriminals will seek your attention by making you believe that you can make a lot of money on the sly, without doing anything. This is clearly an indicator that it is a full-fledged scam.
- Invitation to register in an external link: If the sender of the email you have received invites you to enter your personal data in an external link, be careful: it could be a scam. Do not take the bait.
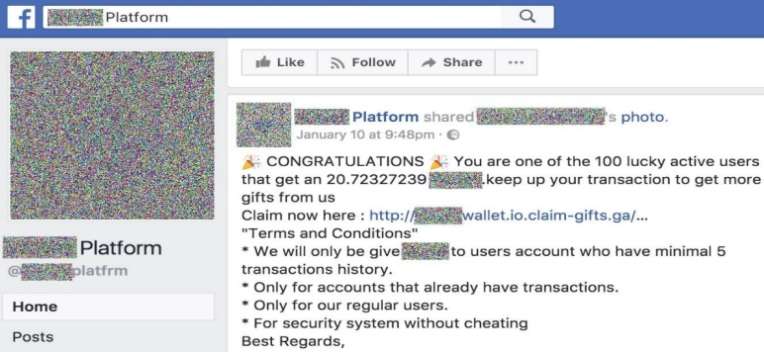
Looking at this other example of phishing, we see that the same thing is clearly happening. The first word is ‘Congratulations’ – you are one of the lucky 100 who have won ‘something’.
It’s clearly a social engineering scam: don’t fall for it.
5. Help or utility
According to numerous studies, most people are willing to offer their help, which makes campaigns to request assistance highly effective.
Unfortunately, hackers and cybercriminals often take advantage of large-scale tragedies to solicit help, even though they are really only benefiting themselves.
One example of this tactic occurred after the New Zealand mosque shooting, a tragic event that claimed the lives of more than 50 people in March 2019 .
In this case, impersonation attempts were detected by cyber actors posing as Westpac, one of Australia’s leading banking institutions and one of New Zealand’s largest banks.
“These emails are NOT from Westpac, and anyone receiving one is strongly advised to forward it to phishing@westpac.co.nz. In addition, if you examine the link provided, you may notice that it redirects to a fraudulent website with the name ‘mothersawakening’. In addition, the account number indicated in these messages is not the correct one for legitimate donations,” communicated Westpac in its official accounts after the scam.
Awareness and training, the best defense against social engineering
In this article, we looked at which emotions cybercriminals seek to arouse in their victims.
Hopefully, it will now be easier for you to detect the malicious emails and separate them from real ones. Always be aware of the emotions described above.
Only by being cautious and patient, examining information and not clicking where you shouldn’t, can you guarantee less exposure to cyber risk on the part of the weakest link: the human being.
Zepo, your best ally in the fight against social engineering

Register your employees.
You can do this manually or through a CSV.
You can create groups of employees based on their level of knowledge and awareness of cyberattacks.

Launch attacks and test your teams.
You will be able to check in real time who falls into the trap.
We create customized templates for your campaigns based on the banks and suppliers you work with. No one will know that it is a simulation.

Train your staff in cyberattack prevention.
Create customized courses on prevention. 3 minutes per month.
No more boring mandatory courses. With Zepo, you will learn and have fun at the same time.